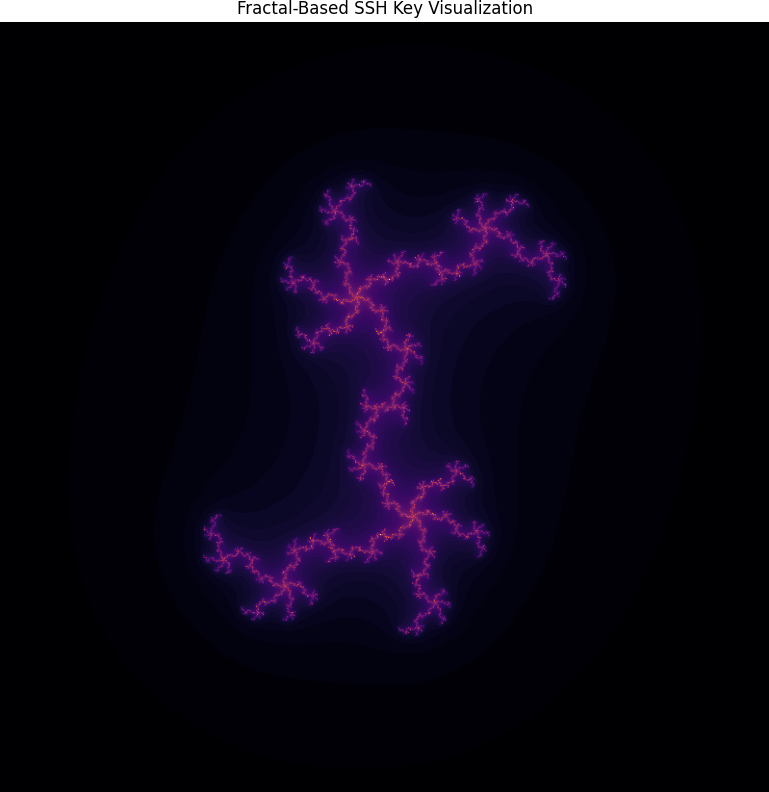
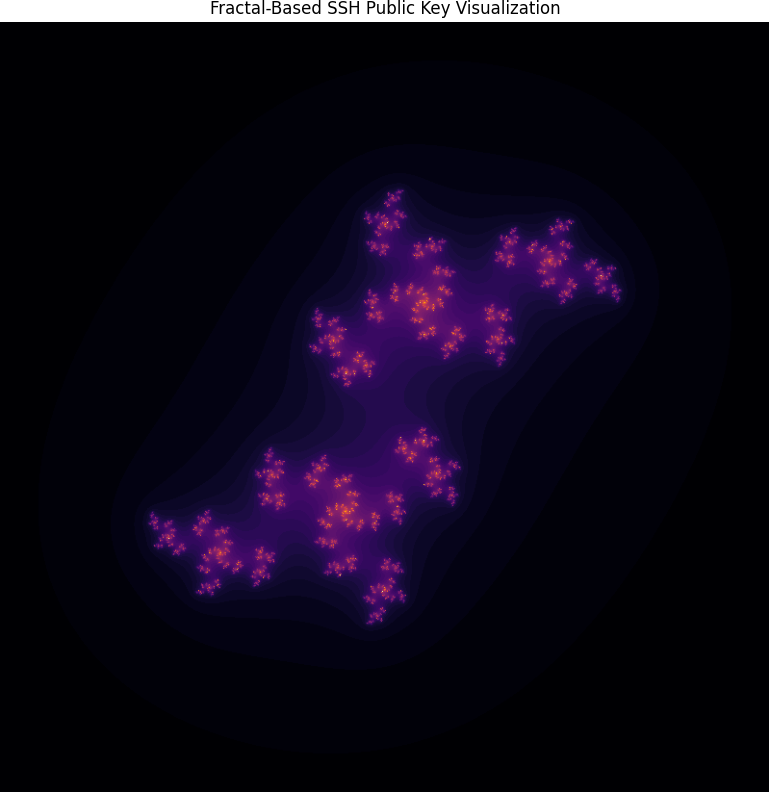
FractalAuth: Nonlinear Approach to SSH Authentication (Part 1)
I’ve been struggling for the past week in how I would present my current passion project, FractalAuth. I must’ve written at least 3 long format posts while continuously updating the project in my private github repository. Regardless, I know this is something I want to share, and when I make the code public, which will happen under Apache 2.0 License when the first major release drops with respect to Semantic Versioning Specification.
FractalAuth
In FractalAuth, I use the Mandelbrot set to create a unique connection between two keys, ensuring they are linked without relying on traditional authentication methods. The system incorporates segments of pre-encrypted, SHA-256 hashed keys into the fractal generation process, increasing entropy. The result is a pair of keys—one original and one "clone"—that are mathematically and visually distinct, yet inseparably linked.The Mandelbrot set’s recursive and deterministic nature forms the backbone of this approach, ensuring that the keys, although visually complex, are intrinsically related. In addition to this, the fractal key generation given an SSH key will always result in the same image. This method allows FractalAuth to establish a form of “proof” of the relationship between the two keys, including but not limited to the deterministic expectation in the key generation algorithm.- It also opens the door to creative verification techniques, such as proving a key via a mobile phone camera app.
Furthermore, the fractal structure introduces a level of error resilience. In the event that the key or its clone becomes corrupted or damaged, the iterative properties of the Mandelbrot set make it possible to recover or reconstruct the key, maintaining integrity throughout the process.
I failed my grade 11 math class..
It was one of those situations, where the teacher had all the pull in the world to pass you if they had seen you applying yourself. Of course, in this case, I hadn’t been trying at all.
| Class Number | Class Name |
|---|---|
| 1 | Physical Education |
| 2 | Spare |
| 3 | lunch |
| 4 | Computers |
| 5 | Academic Math |
Reflections on a Ridiculous Time
As I reminisce, I can’t help but go back to a time in my life that, in many ways, was absolutely ridiculous. Stories fire off in my mind—though, unfortunately, most of them will likely never hear the murmur of truth. They remain an incredible set of memories I share with only a select few people. But I digress.
My PhysEd teacher also doubled as my math teacher, and they weren’t naïve to the fact that I wasn’t applying myself. Many days, I’d skip period one altogether, which meant my day didn’t start until after lunch. My friends and I frequently indulged in activities that, at the time, were far from legal. It wasn’t unusual for me and a good friend to arrive at computer class giggling and a little nervous about how well the Visine had worked.
Despite our questionable pre-class rituals, we shared a genuine interest in computer security and programming. This lined up perfectly with a class focused on teaching Visual Basic. And though our habits might have painted us as slackers, we always showed up—and not only that, we excelled. My mark? A solid 96%. And I wasn’t even trying.
We had fun. This was around the time I started noticing how, with a little effort, people seemed either completely unaware or astonishingly naïve about security. And, honestly, some things never change.
Example One: The Credential Stealer
I wrote a very basic credential stealer in Visual Basic. The process was simple:
- Run the program from my logged-in account.
- Display a fake login screen mimicking our Novell NetWare system.
- When the next student sat down and attempted to log in, the program stole their credentials, logged them to a file on my account, and threw a fake memory error before rebooting the computer.
- Upon reboot, the actual login screen appeared, and the unsuspecting user logged in without thinking twice about the error.
The list of stolen accounts grew by the day. But to be clear, I never used these accounts for anything malicious.
Mr. Coleman’s Discovery
Mr. Coleman, our teacher, was sharp. Somehow, he caught on. Unbeknownst to us, he had a RAT (Remote Access Tool) installed and could monitor any student’s activity at any time. One day, when I logged in to check my ever-growing account list, I found it erased. In its place was a message:
“I’ve caught on to what you’re doing.”
I never got in trouble for it, though. Mr. Coleman asserted his authority, nipped my antics in the bud, and perhaps was even a little impressed. He didn’t escalate the matter or ruin my life over it. So, Mr. Coleman, if you happen to read this—thank you for your restraint. And I apologize in advance for what you’re about to read next.
Example Two: Crashing the Network
Our school’s network included a rudimentary messaging service that no one seemed to know about. My buddy figured out how to send a message to every logged-in computer. Early 2000s mischief ensued as we weaponized this into a denial-of-service attack that crashed the entire network.
For us, it was exhilarating—a feeling of being clever enough to outsmart the adults. We weren’t just “stupid skater kids” anymore. After each crash, the network tech would storm into the computer lab to have a stern discussion with Mr. Coleman. Meanwhile, the two of us, eyes glazed and laughing, would shrug and and play dumb.
I also plomise we did not use any of the harvested accounts to cover tracks when taking down our highschool network.
How is any of this relevant?
Yeah, I was really tripping down the rabbit hole that is my highschool experience. If you review my schedule, you’ll likely gather that since computers was an easy class for me, my entire semester schedule was a joke aside from Math - the last class of the day.
I’m not going to make excuses - By this time of the day, not only was I burning out from previous actions I’d taken regarding ‘extra-curriculars’, but I just wasn’t at all interested. Nothing drew me to the class. It seemed, at the time, pointless.
And damn, I realize how disrespectful it was in hindsight, but I’d be that kid who just slept through the class. So while I was full of rage when I failed it, because a young idiot teen with crazy hormones, I do fully understand why I failed, and why my teacher was not willing to let me make it up by rewriting a test or handing something in. That was for my own good, and I knew deep down that I desserved the fail.
A Final Reflection
Looking back, high school was an insane time, and these antics are only the tip of the iceberg. I’ll have to write more about those years—carefully considering what won’t catch me up in trouble..
But even in the chaos, I learned something valuable: the power of curiosity and how the right kind of teaching can ignite it.
By grade 12, I was retaking grade 11 math - so yeah, I was that guy in a grade 11 class as a grade 12.
For me to be at least intriqued, I needed to be challenged, but I also needed to see a relevant, functual reason for the work. Ineeded that piece of the puzzle. I couldn’t really give a shit for finding a point on a curve, unless there was some reasoning behind finding the point in the first place. I don’t think I’m alone in this one either.
For instance, I’d have taken a much more serious interest in trigonometry if I had known at the time it was paramount in the dessign of vector based aimbots for games such as Counter-Strike..
Counter-Strike was the jam, and it also served as a way to get comfortable with game modification, scripting, and in my case, programming.
The method used back in those days was DLL Injection, Engine and Client Function Hooking, and either DirectX/OpenGL hooking. We were of course blessed with the Half-Life SDK, and this made it a lot easier to reverse engineer the game in the context of client and engine functions. When the game would update, a variable would need to be updated in the hack to properly reference the beginning position of both the data structures describing the client and engine. Otherwise, unless some massive change was made to the game engine, they would just work - utilizing the native game functions to draw custom menus, hooking functions and injecting custom code, then returning the original function so the game was none the wiser.
Aimbots however, that is some serious math. Trigonometry is uesed in almost every aspect, from angle calculation, Distance Calculation, Field of View checking, and Projectial Trajectory Compensation.
Now I get that its asking a lot for a teacher to just make this connection - but I think my main point is, there wasnt a lot relatable with regards to word problems.
If my teacher could have explained how trigonometry would be paramount in designing an aimbot for counter-strike - I’d have been the start of the class
I want to also note that Counter-Strike was a great platform to learn a wide variety of skills that could translate into the real world.
- Scripting with client-side variables in the console
- Game hacking -> Programming in c++, many programming methods, libraries such as OpenGL
- Running servers -> Maintenance, administration,
- Mapping -> Building 3d maps to play in with industry standard software (3dsmax)
- Web Design -> Most clans had a website and or forum, so if you were an active or lead role, you were involved in this
Summer school - not really my thing, so I took grade 11 math in grade 12. This time, I had a different teacher - Mr. Allen, who had different methods, and was able to kindle a drive in me to participate.
Exploring Consciousness and Psychedelics
Wait, what?
It’s probably no surprise that during this age—at least in my generation—there was a significant interest in mind-altering substances. As mentioned before, weed was fairly common despite its legal status, but psilocybin mushrooms were right up there too. Of course, we’re not even factoring in the usual suspects like alcohol and cocaine.
I went full-on hippie during those days—not so much in appearance, but in the way I approached consciousness and drugs. Every night, I attempted to Astral Project, striving to induce out-of-body experiences. I spent countless hours diving into any material I could get my hands on about mind-altering substances. Sites like Erowid, Bluelight forums, and Shroomery were my go-to sources of information.
In grade 9, we had to read Brave New World—and no, I did not read it*. But when I found out it was written by Aldous Huxley, the same guy who wrote a series of essays about his experiences with mescaline (probably via peyote), my interest was piqued. And, for the record, Brave New World is actually a great read. I recommend it.
It wouldn’t have been unusual to find me deep into researching hallucinogens, blasting Infected Mushroom, listening to Terence McKenna ramble about out-of-this-world hippie shit, or combing through the chemical synthesis bibles on tryptamines and phenethylamines by none other than Alexander “Sasha” Shulgin.
The Psychedelic Experience
Anyone who has even a sub to mid-level psychedelic experience is familiar with the constantly breathing, patterning visuals that manifest behind closed eyes, in the dark, or even on solid surfaces.
It’s an incredibly unique phenomenon—distinct from chemical to chemical—yet so similar in its overarching action.
Each compound family offers its own distinct flavor of the experience. The two titans, of course, are:
Ergolines (Lysergamides):
- LSD-25
- ALD-52
- ETH-LAD
- AL-LAD
Tryptamines:
- Psilocin (4-HO-DMT)
- 5-MeO-MALT
- 5-MeO-AMT
- DMT
- DPT
But the list extends well beyond these categories into other realms of psychedelic exploration:
Psychedelic Amphetamines:
- DOM
- DOC
- 2C family (Phenethylamines)
Arylcyclohexylamines (Dissociatives):
- Ketamine
- DXM
- MXE
- 3-MeO-PCP
- 2-Oxo-PCM
Kappa-Opioids:
- Salvinorin A (Salvia divinorum, anyone?)
Regardless of the chemical family, and without diving into the visual madness brought on by deliriants, there’s an undeniable common thread among classical psychedelics:
They all share an affinity for activating the 5-HT2A receptor, the gateway to those profound, mind-expanding experiences.
It’s fascinating how each of these substances brings its own fingerprint to the psychedelic experience, yet they all seem to pull from the same cosmic thread, bending perception in ways that are impossible to describe to the uninitiated. Perhaps I’ll expand one day on my extremely long list of experiences regarding psychedelics.
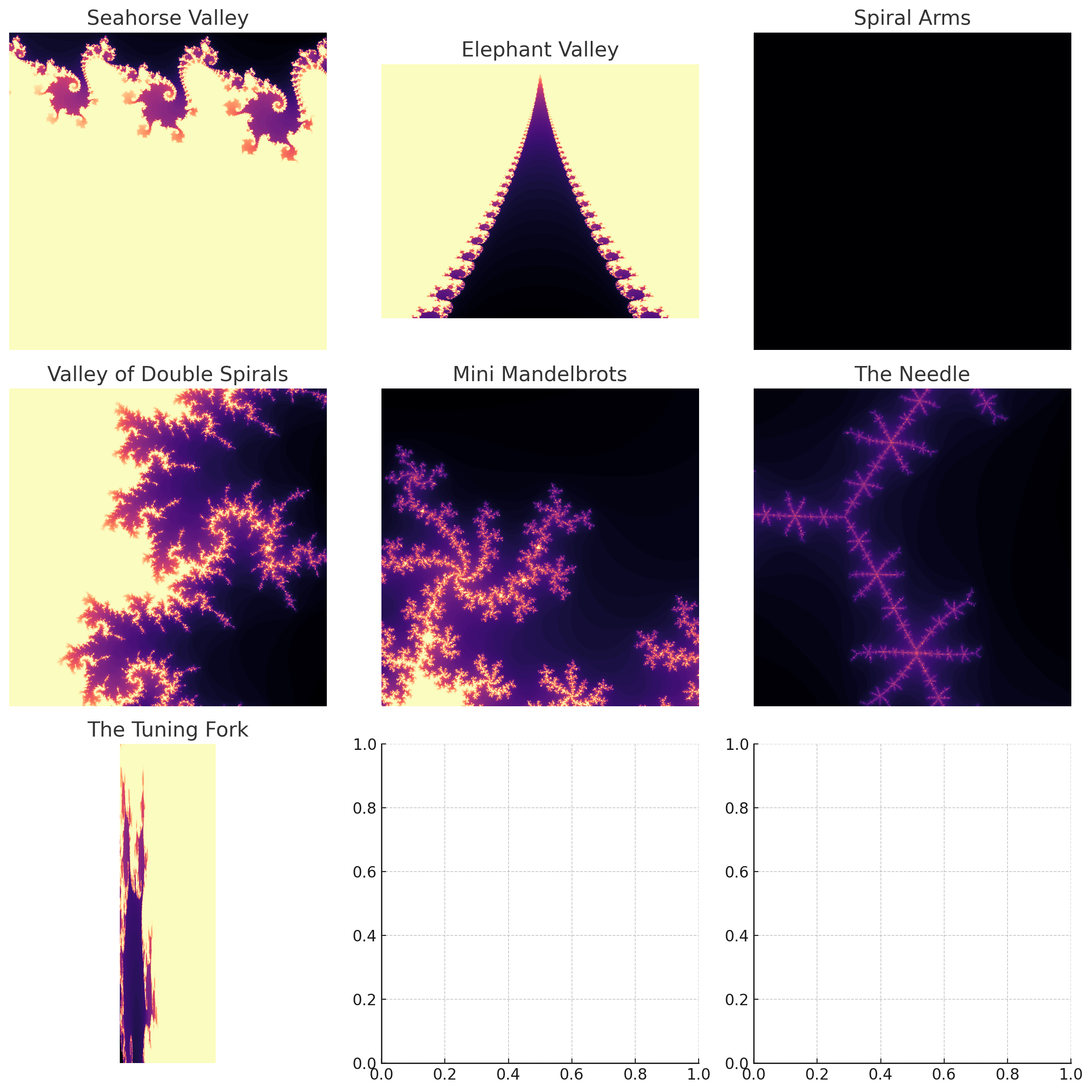
So what is a Fractal?
A fractal is a geometric shape that exhibits self-similarity, meaning that small parts of the shape resemble the larger whole. Fractals are often used to model natural phenomena, such as the branching patterns of trees or the intricate structures of seashells. There are a wide variety of fractal types - all of which are derived from known mathematical functions. This means, we can expect to see deterministic results from these functions, no matter how complex they may seem, mathematically, visually or otherwise.
1 | |
How do Fractals work?
Fractals are created using a recursive process. The basic idea is to start with a simple shape, such as a line segment, and then repeatedly apply a transformation to it. The transformation is typically a function that scales the shape in some way, such as stretching it or rotating it. I would hazard a guess at the most notable example of this being the Fibonacci Sequence
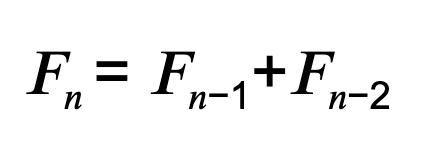
This is a vague explanation but it summarizes the important aspects to keep in mind when definining a fractal - recursive process in the form of a function which scales infinitely in a deterministic way.
But why Mandelbrot?
The Mandelbrot set is a fractal defined by a simple mathematical equation, but its complexity unfolds as you zoom into any of its points. What makes the Mandelbrot set special is its infinite nature—every point on its boundary, no matter how much you magnify, reveals new patterns that echo the structure of the whole.
This self-similarity, recursive, fractal-like behavior, is key to how it can be used in error correction for instance. In fact, I would go as far as to say, it is so incredibly evident that this should be a thing, I expect I am missing something and entirely wrong. And if Im not, maybe I just stumbled into something great.
Mandelbrot in Error Correction
Error correction often revolves around ensuring that the data being transmitted or stored is free of errors and can be restored if something goes wrong. The Mandelbrot set, with its infinite recursive structure, offers a creative and powerful way to approach this problem.
- Recursive Redundancy:
One of the core principles behind error correction is redundancy—adding extra information that can be used to recover from errors. The recursive nature of the Mandelbrot set mirrors this redundancy, where each part of the set contains a miniature replica of the whole. If an error occurs in one portion of the data, the system could reference this self-similarity to reconstruct the lost or corrupted data.
If data is encoded in a fractal pattern resembling the Mandelbrot set, any portion of the data could be reconstructed by referencing another portion. Just like zooming into the fractal where the same structure reappears, corrupted data could be regenerated by referencing a similar pattern within the fractal.
- Pattern Recognition for Error Detection:
Because of the inherent self-similarity of the Mandelbrot set, it could serve as an ideal framework for error detection. The set’s boundary, as it’s zoomed into, maintains a consistency in its shape and structure, meaning that any deviation from the expected fractal pattern could signal an error.
In a system using Mandelbrot-based error detection, data could be mapped to regions of the Mandelbrot set. If the data begins to deviate from the expected fractal pattern, an error would be flagged. The error correction system could then “zoom into” the data at the level of the fractal where the error occurred, using the surrounding self-similar structure to regenerate the missing data.
- Fault Tolerance via Fractal Recovery:
Fractal recovery techniques, inspired by the Mandelbrot set, could ensure that when data is corrupted, the system doesn’t lose it completely. The fault tolerance mechanism would tap into the infinite depth of the Mandelbrot set’s structure, using higher or lower levels of recursion to recover lost data.