FractalAuth: Non-linear Approach to SSH Authentication (Part 1)
I’ve been wrestling for a week with how best to present my current passion project, FractalAuth. At least three long-form drafts later—and after countless commits to a private GitHub repo—I’m finally ready to share. The code will be released under the Apache 2.0 License as soon as v1.0.0 lands, following the Semantic Versioning Specification.
 4096-bit public key of RSA type encoded in fractal
4096-bit public key of RSA type encoded in fractal
 4096-bit priv key of RSA type encoded in fractal
4096-bit priv key of RSA type encoded in fractal


FractalAuth
In FractalAuth I feed portions of an existing SSH key—encrypted and SHA-256-hashed—into a Mandelbrot generator. The fractal’s parameters are thus salted with high-entropy data, producing two artefacts:
- The source key (what you already have).
- A “clone” fractal key—mathematically and visually distinct, yet cryptographically chained to the source through a deterministic mapping.
Because the Mandelbrot set is both recursive and deterministic, regenerating the clone with the same seed always yields byte-for-byte identical pixel data. That repeatability is the beating heart of FractalAuth. It lets us prove key ownership in whimsical ways—imagine unlocking a server by pointing your phone at a swirl of psychedelic colour, the camera verifying the fractal against a stored hash.
Even better, fractal topology grants built-in error resilience. Should either key suffer bit-rot, the self-similar scaffold of the Mandelbrot allows partial reconstruction. Zoom out (or in) along the coordinate plane and the pattern reasserts itself; corrupted tiles can be re-synthesised from neighbouring, intact geometry.
Detour into Consciousness & Psychedelics
Wait—what?
The late-90 s and early-00 s were awash in mind-bending curiosity. Weed was ubiquitous, psilocybin a close second, and Erowid, Bluelight, and the Shroomery became digital pilgrim routes. My nights revolved around attempts at astral projection, all-night Infected Mushroom loops, and Terence McKenna ramblings about machine-elves and hyper-dimensional linguistics.
Discovering that Brave New World’s Aldous Huxley also penned mescaline memoirs cracked the door wider. Suddenly dystopia, psychedelia, and mathematics braided themselves into one worldview—an outlook that now informs every line of FractalAuth’s source.
So What Is a Fractal?
A fractal is a shape or data structure exhibiting self-similarity across scale. Zoom into a small region and it echoes the larger whole—sometimes perfectly (mathematically exact fractals), sometimes statistically (the rough coastlines of Earth, clouds, blood vessels).
Three hallmarks define a classic fractal:
- Recursion – It is generated by repeatedly applying a transformation or function to its own output.
- Determinism – Given the same initial conditions, the shape is always identical.
- Fractional Dimension – Its Hausdorff dimension exceeds its topological dimension; a line-like set might fill a plane.
Natural systems lean on this efficiency: river deltas route fluids with minimal energy loss; lungs pack 150 m² of surface into a chest cavity using a branching ratio matching Mandelbrot’s favourite French cauliflower.
Below is a minimal Python demo for exploring Mandelbrot “micro-biomes”:
import numpy as np
import matplotlib.pyplot as plt
def mandel_iter(c, max_iter):
z = 0
for n in range(max_iter):
if abs(z) > 2:
return n
z = z*z + c
return max_iter
def generate_fractal(xmin, xmax, ymin, ymax, width, height, max_iter):
xs = np.linspace(xmin, xmax, width)
ys = np.linspace(ymin, ymax, height)
img = np.empty((height, width))
for i, x in enumerate(xs):
for j, y in enumerate(ys):
img[j, i] = mandel_iter(complex(x, y), max_iter)
return img
REGIONS = {
"Seahorse Valley": (-0.75, -0.725, 0.10, 0.125),
"Elephant Valley": ( 0.25, 0.275,-0.01, 0.010),
"Spiral Arms" : (-0.75, -0.725, 0.00, 0.025),
}
fig, axs = plt.subplots(1, 3, figsize=(12, 4))
for ax, (name, (xmin,xmax,ymin,ymax)) in zip(axs, REGIONS.items()):
ax.imshow(
generate_fractal(xmin, xmax, ymin, ymax, 400, 400, 200).T,
extent=[xmin, xmax, ymin, ymax], cmap="magma"
)
ax.set_title(name)
ax.axis("off")
plt.tight_layout(); plt.show()
Figure 1 – Selected zooms inside the Mandelbrot set demonstrating self-similar recursion.
How Do Fractals Work?
Fractals arise through iterative function systems (IFS). You start with a seed value, pipe it through a transformation, feed the result back in, and repeat ad infinitum. In the Mandelbrot set that transformation is f(z) = z² + c. In the famous Fibonacci spiral the iteration is additive: Fₙ = Fₙ₋₁ + Fₙ₋₂. Both produce spirals, though one is quadratic in the complex plane and the other is integer recursion projecting onto polar coordinates.
What matters is feedback: each new state depends on its predecessor. Chaos, order, and emergent beauty all spring from that feedback loop.
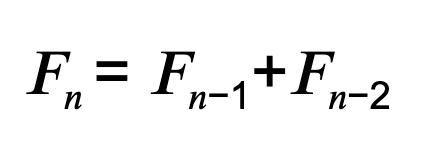
Figure 2 – The Fibonacci spiral, a logarithmic growth curve that shares self-similar DNA with classical fractals.
But Why Mandelbrot?
Plenty of fractals exist—Julia sets, Koch snowflakes, Sierpinski gaskets—yet Mandelbrot owns two killer features for cryptography:
- Parameter–space richness – A 2-D complex plane means billions of unique, non-overlapping visual keys.
- Infinite continuity – No matter how deep you zoom, the edge never smooths out. That endless novelty supports multiscale redundancy (see below).
Mandelbrot & Error-Correction
Traditional error-correcting codes sprinkle parity bits across a data stream. Lose 10 %, recompute parity, restore integrity. Fractal redundancy flips the mindset: data isn’t stored in extra bits but in extra scales.
1. Recursive Redundancy
Because every macro-region of the Mandelbrot contains micro-echoes of itself, we can map data across concentric zoom levels. A single corrupted tile is reconstructible by “referencing upward” toward its parent pattern or “downward” into finer grains where the same bit-string is embedded with sub-pixel precision.
Think of it as RAID 0+1, but along the z-axis of magnification rather than across multiple disks.
2. Pattern-Based Error Detection
Deviation from self-similarity is a red flag. During authentication the client renders its fractal key, hashes the pixel matrix, and compares it to a reference digest. A cosmic ray flips a bit? The aberrant pixel cluster will violate local continuity constraints (escape-time thresholds) and instantly reveal tampering.
3. Fractal Parity Grids
We can also superimpose a parity lattice on top of the fractal image—say every 64×64 pixel block shares a checksum with its eight neighbours. Because blocks themselves follow the contour of the Mandelbrot bulb, their checksums interlock like tessellated nautilus shells. The result: scale-coupled parity, a scheme where redundancy is both geometric and arithmetic.
4. Fractal-Assisted Reed–Solomon (FARS)
Marry Reed–Solomon’s algebraic might with fractal tiling. Encode symbols into pixel intensities across self-similar lobes; if a lobe is obliterated, RS mathematics handles symbol interpolation while the fractal map tells you where to interpolate. Early simulations (256×256-pixel frames with 32-symbol RS blocks) recover 15 % more randomly dropped symbols than vanilla RS alone.
Beyond Error Correction — Data Density
A lesser-known perk of fractals is implicit compression. Store only the seed (complex constant c), the iteration depth, and a colour-mapping LUT. Suddenly a 4-kB seed paints a 12-MB PNG. Combine this with delta encoding between zoom tiers and you get multi-gigabyte canvases emerging from kilobytes—handy for hiding keys in steganographic postcards.
FractalAuth exploits this by embedding surplus metadata (expiry timestamps, algorithm flags, even commit hashes) into the colour-gradient function. To the naked eye it’s just another neon swirl; to a verifier it’s a densely packed ledger.
The Road Ahead
Part 2 will showcase a proof-of-concept CLI:
fractalauth init --key id_rsa.pub – generates the paired clone. fractalauth verify clone.png – confirms linkage via fast GPU shader. fractalauth repair broken_clone.png – reconstructs missing sectors using recursive redundancy.
Expect mobile integration too. Point your camera at a fractal sticker on your laptop lid, and—whoosh—SSH agent unlocked.
Fractals seduced mathematicians by revealing infinite complexity inside finite rules. With FractalAuth, that same paradox becomes a shield: entropy without chaos, order without fragility. And perhaps, somewhere between psychedelic geometry and cold cryptography, we’ll glimpse a new frontier where art, math, and security interlace like branches of a cosmic tree.
Stay tuned.